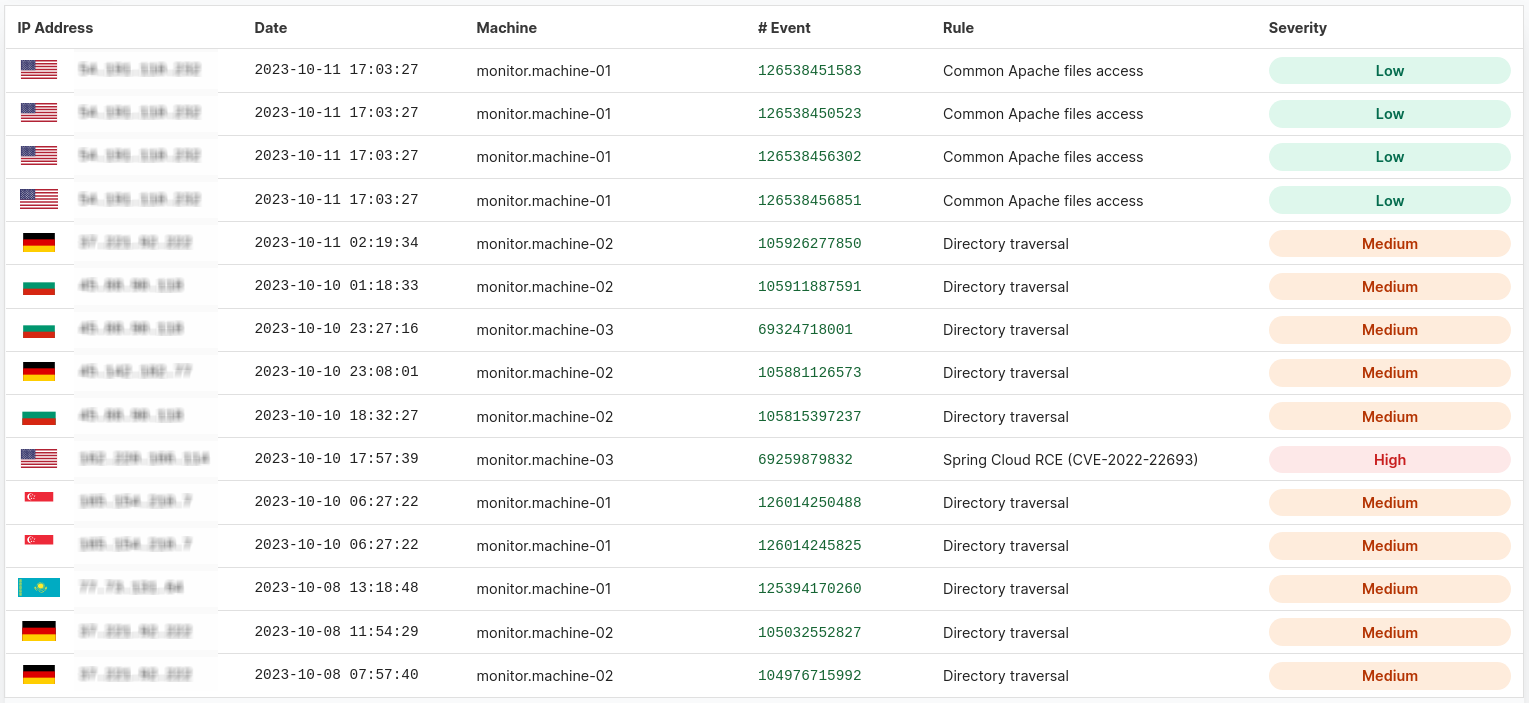
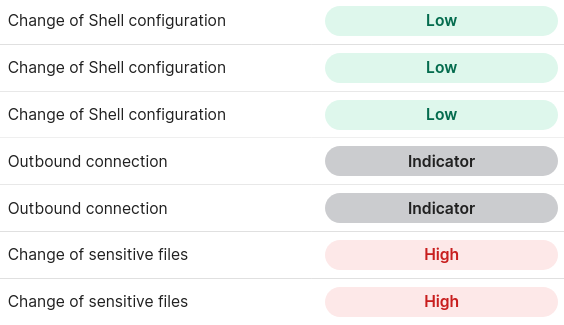
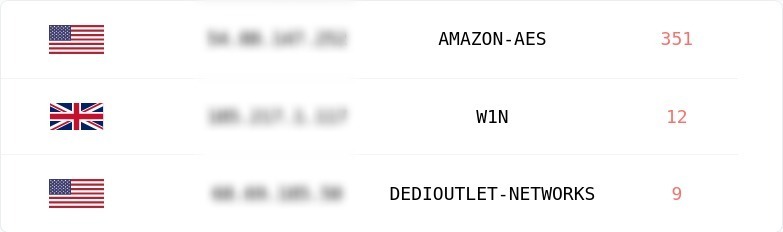
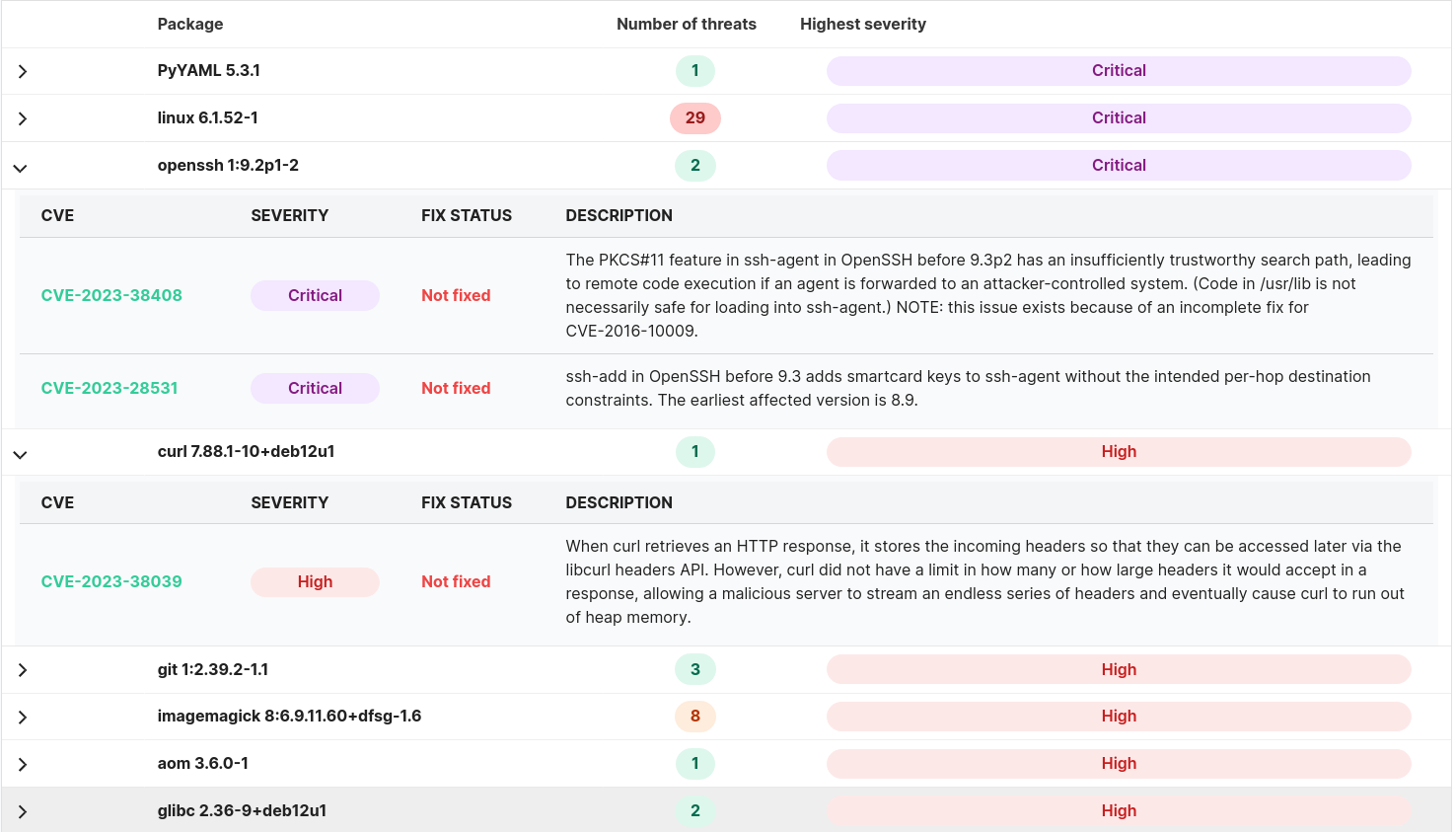
Making cloud deployments safe and observable for everyone.
QDR is a cloud security solution that provides organizations with the right combination of system monitoring, protection, and response capabilities to reduce the risk of cyber-attacks. QDR's continuous observability protects your cloud deployments from breaches and helps proactively discover security blind spots. QDR works with your cloud provider of choice and offers support for environments like bare metal servers, containers, and Kubernetes.